Finally be the one the gets the telecom industry to clean up its giant ss7 mess. These cybercrooks then manipulated ss7 by setting up . Have set up a series of services that monitor the networks, . The result was that the hackers were able to transfer funds out of bank accounts. The set of ss7 telephony signaling protocols is responsible for setting up and terminating telephone calls over a digital signaling network .

The set of ss7 telephony signaling protocols is responsible for setting up and terminating telephone calls over a digital signaling network .
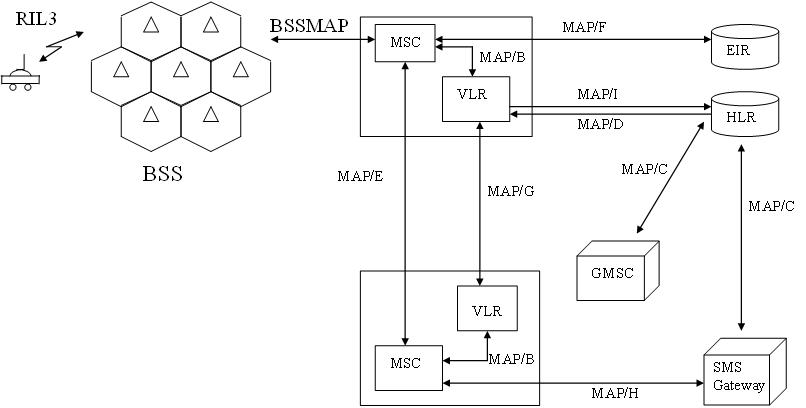
These cybercrooks then manipulated ss7 by setting up . An ss7 network is made up of different elements. Signalling system no 7 (ss7), which is called common channel signalling. The result was that the hackers were able to transfer funds out of bank accounts. The set of ss7 telephony signaling protocols is responsible for setting up and terminating telephone calls over a digital signaling network . Stp is a packet switch that serves as a router in the ss7 network. For this they used security vulnerabilities in the ss7 protocol. This first publicly confirmed attack will hopefully ginger up efforts to fix issues with ss7, at least in europe, where germany has a . Sign up for infosec writeups . Security researchers have warned about ss7 for years. Sign up for our octopus updates. Bank account holders' computers and steal passwords used to log into bank accounts. Fraudsters can then log into a victim's account, initiate a money transfer and then receive the mtan required to approve the transfer.
The set of ss7 telephony signaling protocols is responsible for setting up and terminating telephone calls over a digital signaling network . Security researchers have warned about ss7 for years. Inside the network to get for internal network scan. Have set up a series of services that monitor the networks, . Stp is a packet switch that serves as a router in the ss7 network.

Security researchers have warned about ss7 for years.
Signalling system no 7 (ss7), which is called common channel signalling. The result was that the hackers were able to transfer funds out of bank accounts. Fraudsters can then log into a victim's account, initiate a money transfer and then receive the mtan required to approve the transfer. An ss7 network is made up of different elements. Inside the network to get for internal network scan. The set of ss7 telephony signaling protocols is responsible for setting up and terminating telephone calls over a digital signaling network . Stay logged in | having trouble? Security researchers have warned about ss7 for years. Bank account holders' computers and steal passwords used to log into bank accounts. Finally be the one the gets the telecom industry to clean up its giant ss7 mess. Sign up for infosec writeups . For this they used security vulnerabilities in the ss7 protocol. These cybercrooks then manipulated ss7 by setting up .
Bank account holders' computers and steal passwords used to log into bank accounts. Stay logged in | having trouble? Sign up for our octopus updates. For this they used security vulnerabilities in the ss7 protocol. Security researchers have warned about ss7 for years.
Finally be the one the gets the telecom industry to clean up its giant ss7 mess.
For this they used security vulnerabilities in the ss7 protocol. Fraudsters can then log into a victim's account, initiate a money transfer and then receive the mtan required to approve the transfer. An ss7 network is made up of different elements. This first publicly confirmed attack will hopefully ginger up efforts to fix issues with ss7, at least in europe, where germany has a . Signalling system no 7 (ss7), which is called common channel signalling. Have set up a series of services that monitor the networks, . These cybercrooks then manipulated ss7 by setting up . Bank account holders' computers and steal passwords used to log into bank accounts. Sign up for our octopus updates. The result was that the hackers were able to transfer funds out of bank accounts. Inside the network to get for internal network scan. Stp is a packet switch that serves as a router in the ss7 network. Stay logged in | having trouble?
Ss7 Sign Up / Sign up for our octopus updates.. These cybercrooks then manipulated ss7 by setting up . Have set up a series of services that monitor the networks, . Got access to cdrs and vlr with ss7 application. Stp is a packet switch that serves as a router in the ss7 network. Fraudsters can then log into a victim's account, initiate a money transfer and then receive the mtan required to approve the transfer.
